IT Security Pain Points
Talking about IT Security is one of the hardest topics for CEOs and CIOs to wrap their minds around. Not only is it a multi-leveled and complicated topic, but it is also associated with increased change and increased expense. It is a topic that requires silos within the business to be broken down. It requires that all employees understand each protocol and process thoroughly.
When we meet with a business to discuss their IT security, we understand the trepidation we are walking into. That is part of why we have developed our unique, business-focused approach over the years. We present a long-term strategy based on actual audits we have implemented for that specific company. This assists in making individual tactics make sense. The same holds true for proposed investments. What can seem overwhelming becomes more manageable when it is broken down and fitted to an over-arching strategy and clearly defined goals.
In addition to cost and the general unsettled feeling of change, our clients also worry about the time and expense of training employees. New protocols and processes are beneficial, but the thought of comprehensively training all employees can seem daunting. Additionally, we are often in meetings where a member of our client’s team will say they do not have the bandwidth to be able to create these new protocols and processes. That is why, in addition to offering IT Security Awareness Training (SAT), we also will create Standard Operating Procedures to ensure all new security protocols are followed by and accessible to everyone. We cover everything when we work with a business.
Our managed IT security services partnerships usually begin the way most of our relationships begin. Someone calls our 24/7 HelpDesk either because they are concerned about their company’s cyber security or because they have experienced a breach of some kind and need help. Our experienced HelpDesk operators know how to get a productive conversation started, and, often, this leads to the opportunity for us to audit the company’s entire IT system, from hardware to software to networking.
The Problem
According to a recent study by Thomasnet.com, the top threat manufacturers have to deal with today is cybersecurity breaches. This includes everything from ransomware and malware attacks to a tactic called CEO fraud, where the attacker manages to buy a very similar domain and make emails look like they are coming directly from a company’s CEO. There is good reason for businesses across all sectors to be concerned about IT security issues. If you have been putting IT security on the back burner, here are some facts to consider about how an IT security issue can impact your business:
- Reputational damage: This can occur in many different ways. A ransomware or malware attack can completely cripple an institution, meaning customers won’t get responses or the services they need, phonecalls may not go through, and more. If the attack also includes email and/or social media, reputation damage can seem irreparable.
- Management time: Management needs to spend time doing damage control on every level of the company’s existence. Customers or clients need to be alerted without alarming them. The attack itself needs to be dealt with. Decisions need to be made about how to prevent attacks like this in the future and how to work around the current situation.
- Customer loss or churn: As mentioned above, if a customer is left high and dry during a cybersecurity event, their compassion will not always be their top priority. Furthermore, if the breach causes the lost of client or customer personal data, that will further inspire them to move to another company they deem safer.
- Financial cost: Tax fraud, CEO fraud, and ransomware attacks simply cost money, plain and simple. In some cases, the cost to get a business back up and running is too much of a burden for that business to be able to bear.
A Medieval Solution to a Modern Problem
The risks are real, but we do not focus on the potential dangers. We focus on the business and look for vulnerable spots where an attacker may find success. Ironically, our approach can be compared to a methodology from the Middle Ages – protecting the castle. Technically, this approach is called “Defense in Depth.”
If a company’s IT existence is the castle and cybersecurity breaches are the dragons or the robbers, how can you protect the castle? Just the way people in the Middle Ages protected theirs. Multiple layers of security, primarily proactive in nature.
For our clients, we help build all of the “castle’s” defenses. We make sure the watchtowers are actively manned at all times. We make sure there are limited, guarded entry points, and we make sure the outer walls and inner walls are strong. Credentials and passwords are always checked and confirmed, and that’s assuming anyone can get past the moat without being noticed. Our partnerships are based on spotting potential trouble before it even comes close to approaching the castle walls.
In order to build the right kinds of defenses, we first need to understand what we are working with. Instead of simply powering in and imposing our recommendations on a company, we first conduct an IT security audit.
The QualityIP IT Security Audit
No matter what started the conversation, our audits are comprehensive. In the business world, 97% of IT security breaches could have been prevented with the right steps and the right technology. As we begin the process of auditing a company’s hardware, software, and other assets, we are looking for weaknesses that could allow breaches to happen. That includes a lack of company-wide security processes and protocols, software and equipment that is either out of date or not maintained/updated consistently, and inefficient training of all staff members. Specifically, we look at the following:
- Security Awareness: When was the last time your team was educated regarding data security, email attacks, and your company’s policies and procedures? A security structure is only as strong as the weakest link. We make sure every employee knows the basics to keep themselves and the company secure.
- Email: Are everyone’s email passwords strong? Are the passwords reset often? Is data encrypted? Can your staff identify phishing emails and potential malware or ransomware attacks?
- Advanced End-Point Security: If you are still using McAffee or Norton Anti-virus, we probably will recommend you enhance and elevate your endpoint security. The technological solutions we are able to offer now are phenomenal and essential.
- Multi-Factor Authentication: We make sure a company we are auditing utilizes multi-factor authentication in as many instances as possible. Just as Google and social media sites are increasingly requiring phone numbers or other identify conformation to protect user data, we want to make sure companies are doing the same for their websites, data storage, email, and social media platforms.
- Computers and Other Devices: This one is often so obvious it’s easy to miss if you are enmeshed in the every-day workings of a business. If someone were to walk into your business, would they be able to simply access data on an available computer? Are your computers password-protected?Often this step gets missed, even at companies where computers are out in the open and easily accessible.
- Firewall Inspection: In our audit we carefully evaluate the status of your firewall. Is your current firewall software assisting with intrusion detection and intrusion prevention? Is it up-to-date? Has it been maintained consistently and properly?
- Did you know your data and passwords can be posted to the dark web without anyone at your company knowing? Part of our security audit is to implement research to make sure your data is secure no matter where in the online world someone goes.
The QualityIP IT Roadmap
After assessing all parts of your hardware, software, and networking, we will develop a comprehensive month-by-month strategy with a proposed budget. The roadmap takes all of the weak points we found and proposes methodologies for fixing each one, with the top priorities indicated first. For each tactic we indicate what the budget will be, and that way we avoid any surprises down the line.
Regulatory Compliance
In addition to strengthening facets of your enterprise that are at risk, we will also ensure your business meets regulatory compliance goals. Regulatory compliance is a necessary part of business today, but for a CEO or CIO responsible for so much of a company’s operations, handling regulatory compliance can represent a big headache. As with so much in operations, the target is always moving and one mistake can create a chain of serious problems.
One of our services as a managed services provider is to take care of IT-related regulatory compliance goals for you. The benefits of meeting regulatory compliance guidelines are numerous. In addition to avoiding fines for non-compliance, which can be substantial, your business will:
- Increase financial security
- Increase protection against data breaches
- Be able to operate in emergency conditions
Taking these responsibilities off of a CEO’s or CIO’s shoulders is a significant benefit in partnering with QualityIP over the long-term. Avoiding the data breaches and penalties also can be a lifesaver for businesses of any kind.
Managed IT Security | We’re Your Guy
QualityIP is does not just offer customized solutions to our clients. The way in which we work with our clients is also unique.
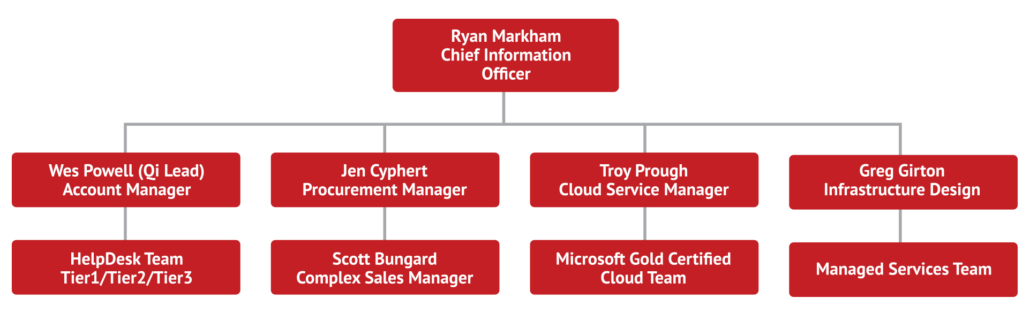
QualityIP has over twenty account managers on our staff. Our clients are all assigned an account manager first. This person is responsible for essentially becoming a member of your team. They are “your guy” for any IT question or decision that arises. Whether you have questions about procurement, the cloud, or the strength of a password, your account manager will walk you through what you need to know.
The account manager is your designated contact, but that does not mean he or she works alone. At QualityIP we often use the phrase, “It takes a village.” Your account manager or your virtual CIO will be supported by our procurement team, our managed cloud team, our IT security team, and more. The account manager will coordinate any specialists that you need to make sure everything in your IT infrastructure remains integrated and compatible. You will also be able to see how all of the specialists will work together in your IT roadmap.
If anyone in your business has a concern or a question, our contracts make our HelpDesk accessible to everyone on your team with no invoicing per contact. That relationship is part of your monthly comprehensive investment. Our HelpDesk is operated by experts and is available 24/7. This helps accommodate businesses that allow remote work and/or flex time.
Our objective is to make sure you never need us, because we strive to create proactive solutions that will prevent problems before they become problems. However, when you need us, we are always there.
The NIST Cybersecurity Framework Overview
We are guided in our work by the National Institute of Standards and Technology. They have established a framework that delineates what needs to be evaluated and improved upon regularly in order to maintain a company’s IT security.
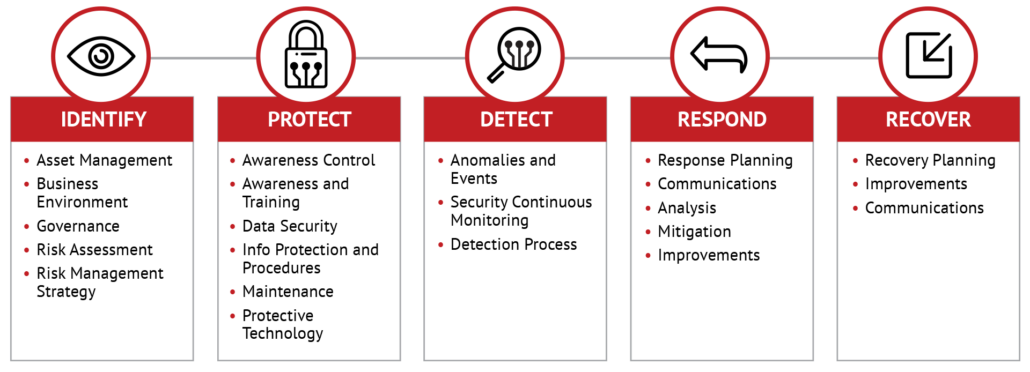
Partnering with us means we are responsible for all facets of this framework, from assessment to implementation to communications about the protocols and processes we are implementing. Our business is devoted to offering the best customer service possible, and when we can take anything off your shoulders where IT is concerned, we certainly will.
Cyber Security Security FAQs
Is my business really at risk for security breaches?
Unfortunately, any business or organization that stores data is at risk for phishing, malware, or other types of security breaches and attacks. It is the dangerous part of living in the digital age.
What is cybersecurity?
Cybersecurity is the overarching term used for the action of protecting hardware, software, and networks from digital breaches and attacks. It is also referred to as IT security.
What is malware?
Malware is a combination of two words, like so many terms in IT are. In this case, malware is a combination of the words “malicious” and “software.” Malware is a code created by a hacker or a bot that can infiltrate an IT system usually via an unprotected network. Malware can impact almost any part of a company’s IT, from networked environmental controls to data security.
What is phishing?
Phishing is an attempted security breach that is implemented via email. Often, a phishing email will look like it is from a trusted domain, and sometimes even a specific person within a company. There is often a zip file to open or a link to click that will ask for personal information like a social security number or a credit card number. An important part of our SAT is teaching employees how to spot phishing attempts and what to do about them.
Does QualityIP force companies to use specific security hardware or software?
No. QualityIP strives to meet companies where they are. If a system is not performing optimally we will note that in our audit and we will make recommendations. Our procurement team is there to assist with ordering, setting a shipment date, and installation. However, we will not force your business to invest in any specific manufacturer’s products.
I have a security breach problem right now. What should I do?
Contact us immediately. Even if you have never contacted us before, our dispatcher team and HelpDesk team will get one of our experts on your case immediately. The first step is to mitigate the problem, and once that has occurred, we will talk to you about how similar events can be prevented in the future.
Why QualityIP?
QualityIP differentiates ourselves from other managed service providers in the following six ways:
- Collaboration We are committed to a constructive, team-oriented environment, gathering varied perspectives, sharing knowledge, and building effective partnerships.
- Continuous Improvement We strive for operational excellence through ongoing development of our staff and organization as a whole.
- Innovation We encourage creative and critical thinking in the development of technology services and solutions.
- People We listen to, respect, and care for our staff, and one another, both professionally and personally.
- Service We strive to provide excellent service by being consistent, agile, reliable, and accessible to all.
- Transparency We leverage open communications and thoughtful business processes to be accountable in our interactions and our work.
We make transferring to our services easy. We are on your team as soon as we start working with you, and that means we make everything as effortless and seamless as possible. If this sounds like a partnership you would appreciate, contact us today.
We look forward to talking with you!
Does Your IT Need TLC?
If you’re ready to boost your business and say goodbye to IT concerns, contact QualityIP. As an award-winning full-service IT support and consulting company in the Naples, FL, area, we have the experience and expertise to provide your business with the support it needs to grow.