Quest Diagnostics Data Breach: The Inside Scoop
December 22, 2016 | Business IT News, Tips and Information
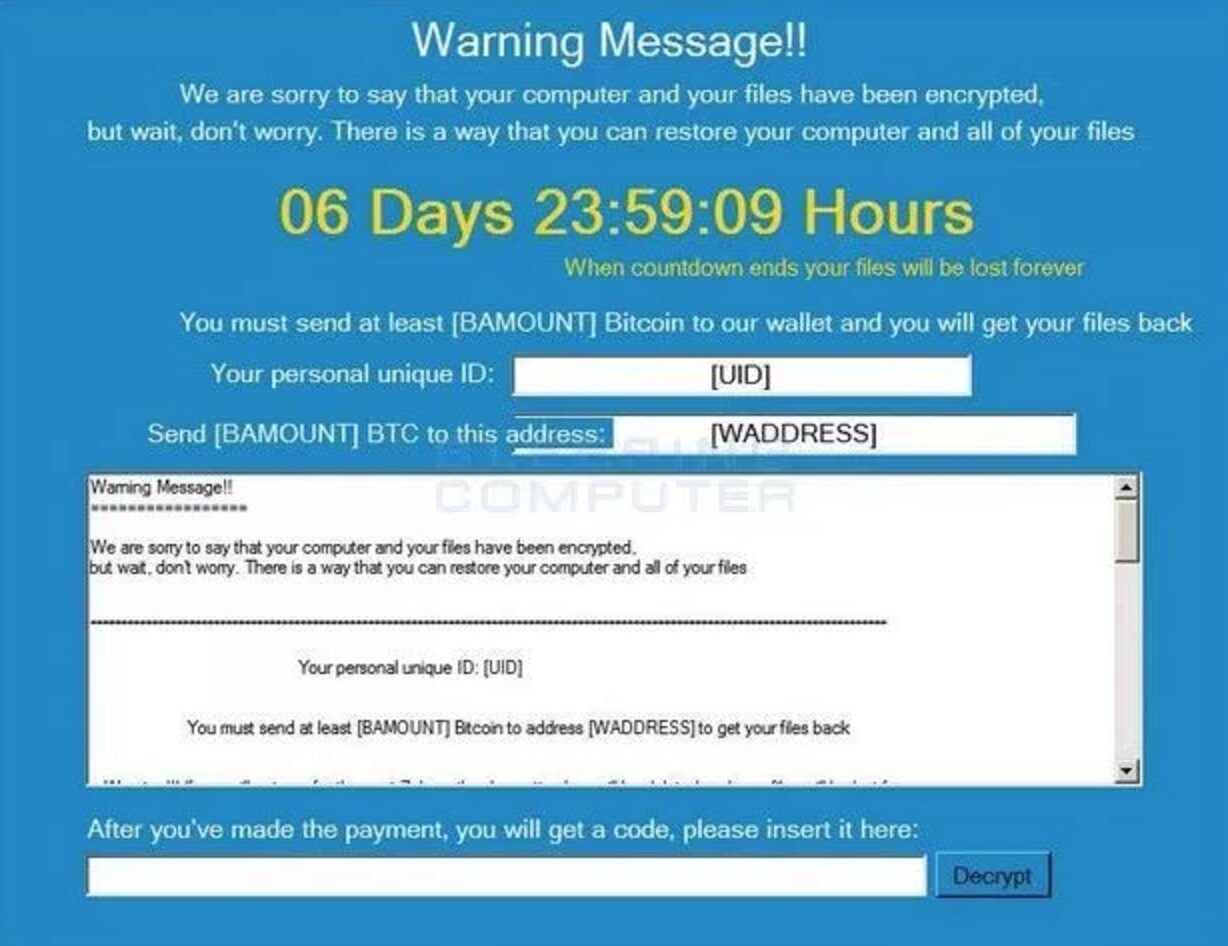
HomeQuest Diagnostics is the latest healthcare industry victim to suffer from a data breach at the hands of hackers seeking to steal valuable personal information and other enterprise data. In a recent December 2016 statement, Quest Diagnostics, Inc. stated that…